- Make a backup of the following files:
- a. C:\InfoShare\Web\Author\ASP\web.config
- b. C:\InfoShare\Web\InfoShareWS\web.config
- c. C:\InfoShare\Web\InfoShareSTS\Configuration\infoShareSTS.config
- d. C:\InfoShare\Web\InfoShareCS\web.config (TD14+ Only)
- Replace in the web.config the Thumbprint with the thumbprint from the renewed certificate.
- Open Internet Information Services (IIS)
- Open Server Certificates
- Locate the renewed Certificate and open it
- Go to the details tab > Locate the Value Thumbprint > copy the value (remember the Control Character at the beginning of the Thumbprint value, to make sure you haven't copied it paste it into a cmd prompt window first, it should not have a "?" in the beginning.)
- Update the web.config files from step 1a and 1b (it occurs twice in both these files)with the new thumbprint values ***Note: the thumbprint value has a control character as the first character, the best way to identify it would be to copy the thumbprint into a cmd prompt.
- Update the infoShareSTS.config from step 1c with the new thumbprint values.
- Open the component services>Computer>My Computer>COM+Applications and shut down "Trisoft-Infoshare-Author"
- Open Internet Information Services and stop
- TrisoftAppPoolInfoShareAuthor (TrisoftAppPoolISHCM TD13+)
- TrisoftAppPoolInfoShareSTS (TrisoftAppPoolISHSTS TD13+)
- TrisoftAppPoolInfoShareWS (TrisoftAppPoolISHWS TD13+)
- TrisoftAppPoolISHCS (TD14+ Only)
- Rename C:\InfoShare\Web\InfoShareSTS\App_Data\IdentityServerConfiguration-2.1.sdf to for example C:\InfoShare\Web\InfoShareSTS\App_Data\IdentityServerConfiguration-2.1.sdf.previous
- Open the component services and start Trisoft-Infoshare-Author
- Open Internet Information Services and start
- TrisoftAppPoolInfoShareAuthor (TrisoftAppPoolISHCM TD13+)
- TrisoftAppPoolInfoShareSTS (TrisoftAppPoolISHSTS TD13+)
- TrisoftAppPoolInfoShareWS (TrisoftAppPoolISHWS TD13+)
- TrisoftAppPoolISHCS (TD14+ Only)
-
Login into the web UI and a new IdentityServerConfiguration-2.1.sdf file should be created containing the correct values of the new certificate's thumbprint and subject name.
If the SDF file is not recreated - close browser entirely, remove cookies and session and got to the IIS page.
*** note if Content Delivery is involved re-check relying party as it is stored in the SDF file ***
New certificate (change of subject and Thumbprint)
- Execute Above procedure +
- Open STS Website https://Servername.domain/ISHSTS --> Key Configuration
-
Update the Signing certificate by selecting it from dropdown.
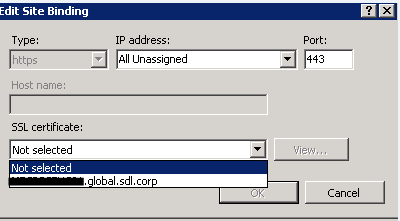
Binding to Port 443
The HTTPS protocol is secured with a certificate. This certificate can also expire and when it does.
-
- Open a Remote Desktop Connection to the Architect Server
- Open Internet Information Services
- Expand <Computername> > Sites > Default Website
- Right click on Default Website and choose Bindings
- Select HTTPS and click Edit

- Make sure that the correct certificate is selected from the dropdown.
- If you have ADFS authentication, make sure to update the replying parties for ISHWS for the client tools to connect successfully.



